Static Analysis #
Static analysis, also called static code analysis, is a method of computer program debugging that is done by examining the code without executing the program. https://searchwindevelopment.techtarget.com/definition/static-analysis
In this post we will look for sensitive information stored in the website like passwords, API keys etc.
Find Javascript Files #
There are multiple ways to gather Javascript files in the target website, In this post i will share it to you.
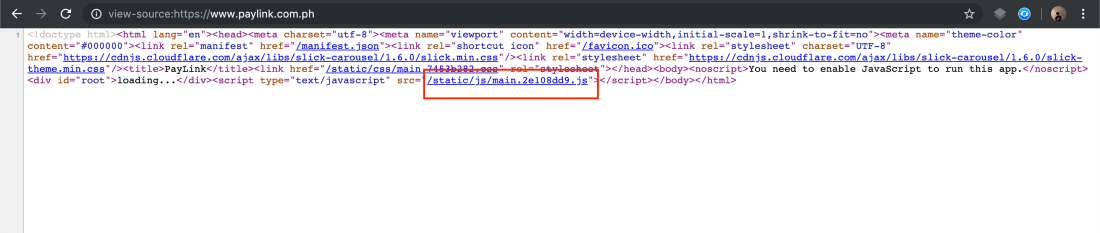
Download the Javascript File #
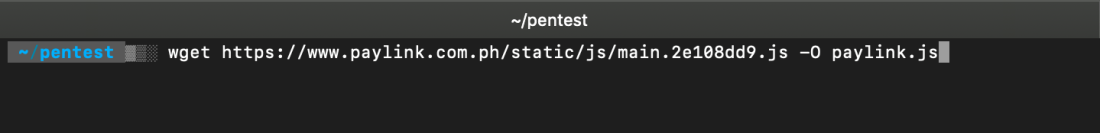
Beautify the file #
npm install js-beautify
You can Use any Javascript beautifier, Once you install js-beautify run the following command to Beautify the Javascript File.
js-beautify paylink.js > paylink-clean.js
Now, Open your Favorite Text Editor and Start Finding the needle in the haystack.
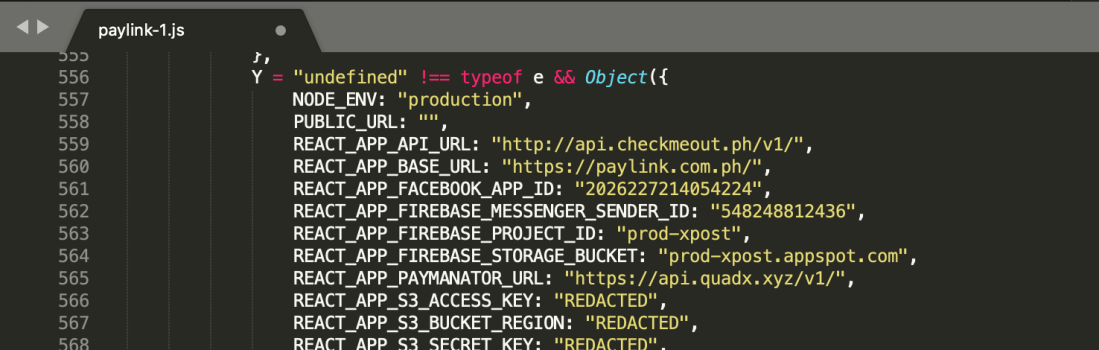
Check the credentials using aws-cli
pip install awscli
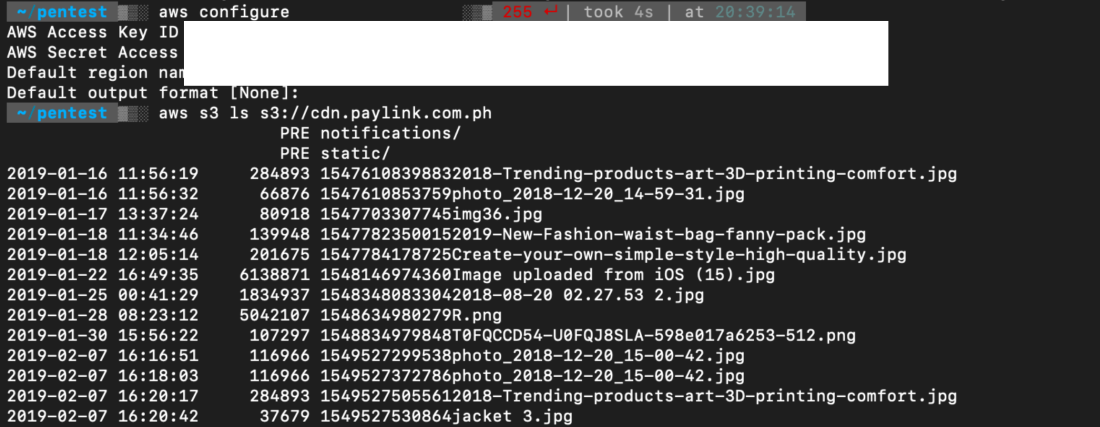
Using the credentials gathered via awscli #
Few Minutes after Submitting, QuadX Immediately Addressed the Issue and the Vulnerability was Fixed Few Hours Later, Giving the Points i needed to Top the Leaderboards at Secuna.
Kudos to QUADX for being transparent about the remediation timeline, I love the fast Response ❤️ ❤️ and to Secuna thank you so much for building this Awesome Cyber Security Testing Platform.
Did you Learn Something? Share this! #sharingiscaring
